Primer
Many “guides” are published on the Hacker Simulator Steam Community. At a high level they do provide the steps, by providing bullet points on the basic 5 steps and leave it up to the player to figure out how to implement the steps on their own. I highly recommend this be the way everyone play the game. Click around, see what everything does. I personally don’t like guides that handhold someone all the way through every step of the game because they take away from the fun, awarding gratification one receives once the solution is figured out. But there are times even I need help trying to understand what to do in any game. This guide provides the step-by-step on how to phish on the Steam game, Hacker Simulator. Use at your own risk. 😁
I realize I could include a few more screenshots of every aspect of the game, but I'm leaving some of these details out so it allows the reader/player to do some figuring out on their own.
Sleep On It
First things first. The only way to phish is if you have the person’s name given to you by a contract in Ziscord. You’ll see a sentence similar to, “The target is named Danny Boi”. If you don’t see this sort of statement in the Ziscord contact’s chat, then either you’ve not progressed this far in the game or, like me, I didn’t think to sleep to get my next set of contracts when I first started, so consider sleeping.
Once you have the targets name, copy and paste that into the Fishbook search field and press the ‘Search’ button and WHAMO! You have your phising target.
Weaknesses (Interests)
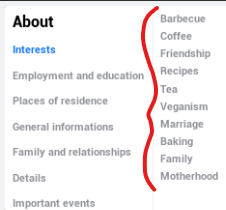
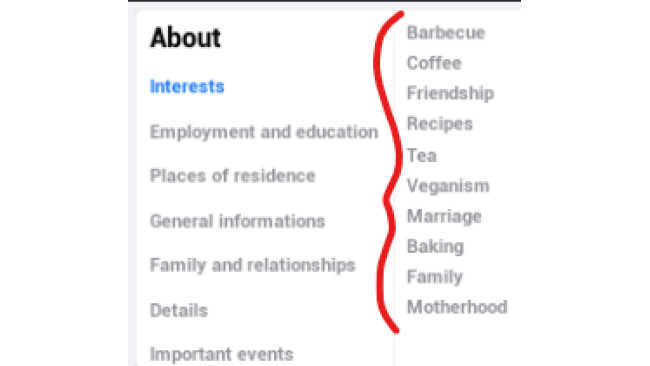
Study the target’s interests, also known as ‘weakness’, located on the target’s page. The first time you review them, they’re located almost dead in the middle of the page, in the column to the right of the ‘About’ section.
Interests are random but will contain words like, ‘Barbecue’, or ‘Friendship’, or ‘Veganism’. You will want to study this list and figure out what category of words they have the most of. More on categories next.
Categories Of Weaknesses
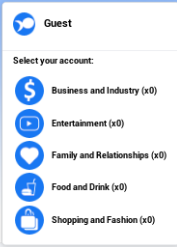
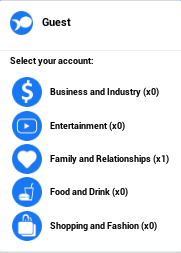
If you look to the far right of Fishbook, you’ll see a section that has the word ‘Guest’ at the top of it. In the lower portion of this section there are five categories.
Based on the target’s most common set of words, their most common interests fall within one of these categories. For example, if most of the words revolve around food, then their ‘weakness’ would be ‘Food and Drink’.
Pro Tip (Spoiler): If there are generally 5 or more words that represent the category, then 99% of the time this is the 'weakness' you need to keep track of.
Buying Fishbook Accounts On The BackStore
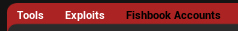
Now that you understand what the Fishbook target’s weakness (I mean interests), travel back to The BackStore and look at the top of the page, where the big red header bar is. At a minimum, you should see the ‘Tools’ and ‘Fishbook Accounts’ options. Click the ‘Fishbook Accounts’ option and you will see all these same categories you saw on the top right of the Fishbook screen.
NOTE: These really aren’t accounts, they’re just messages you buy on BackStore to use against Fishbook targets. You’ll see what I mean in a minute.
PRO TIP: Don’t buy more than what you need. Just buy the ‘account’ you need and go back to Fishbook. It can be easy to softlock your progression if you run out of money, so don’t be greedy here.
Confirm You Have The ‘Fishbook Acccount’
Navigate back to Fishbook by reentering the target’s name. You should still have their name copied in your clipboard, so just paste it in the Search field again and hit ‘Search’.
Looking again at the top right of Fishbook, you will see the category, that you just purchased from The BackStore, will now have a (x1) next to it. If you don’t see this then you probably didn’t buy the ‘account’ so go back and purchase it at the store.
Listen With 'netcat'
Before you do anything else in Fishbook, open a terminal, or navigate back to your primary terminal window and start ‘netcat’. This tool listens to the network traffic happening on Fishbook and, if your phishing attempt is successful, you will eventually connect to the target’s computer, so make sure to keep your terminal in view alongside your browser.
Back To Fishbook Where The Phishing Happens
OK, now that your deck is primed and ready, you want to begin the Phishing attempt.
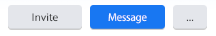
1. Click the 'interest/weakness' category in the top right, under 'Select your account' and this will then ready the 'Message' button.
2. The ‘Message’ button will enable, going from gray to blue. Click it and a chat window will pop open with a canned message in the chat. (This is what I meant by you're buying a message moreso than an account.)
3. Click the Send button in the chat window and wait for the target to reply back. This takes approx 10-15 seconds to see a response.
4. If done correctly, your 'netcat' terminal window will take another 10-15 seconds to connect you to the target's system.
PRO TIP: If you succeed or if you fail...
If the target responds in the positive (i.e. “I will!”) then you have succeeded at the phishing attempt, but this doesn’t conclude your actions. Wait a bit longer and you’ll have access to the target’s computer from your terminal. If the target responds in the negative (i.e. “I’m reporting you!”), then you have failed at your attempt and the contract.
Performing The Requested Deed
Once you’re on the target’s computer, just finish out the request provided by the contact on Ziscord and disconnect from the target’s machine before you get caught.
Wrap Up
Hopefully this helps those of you still struggling with figuring out how to actually successfully phish.
If you have any questions, comments or recommendations, let me know. I'll be happy to make revisions and corrections.
Please go gentle as this is my first guide. Hope it's not too bad. 😊
Source: https://steamcommunity.com/sharedfiles/filedetails/?id=3062356677
More Hacker Simulator guilds
- All Guilds
- Credit goes to Corporal Punishment for this. Python Code for decrypting non hex
- Guide for most early stuff if you are struggiling
- Phishing cheat sheet
- Decrypting tool
- making code play this game for me ep. 1
- Alphabetized Malware Upload List
- Cheat Sheet & 10/10 Comet jobs: step-by-step
- A few tips